File transfer protocol is a way to transfer files over a network.
We need to secure our transfer over a network.
There are two types of protocols- SCP and SFTP.
SFTP- Secure file transfer protocol
SFTP is an extension of older SSH. It is Secure FTP or Secret FTP.
SCP- Secure file copy.
There are some advantages of SFTP over SCP.
For e.g.: Sftp can resume the interrupted transfers but it is not possible in SCP.
Also SFTP has remote file removal and is more independent than scp.
SCP is confined to UNIX only whereas SFTP can be used on any operating system.
Sftp can work on any stream but Scp can work on only SSH.
On the other hand, Scp is faster than Sftp. It is so because SCP implements a more efficient transfer algorithm. In Scp, it is not required to wait for packet confirmations. But due to this fast speed, Scp is not able to stop any transfer. Scp transfer cannot be stopped in between without terminating the session.
Scp is better to use if one wants to upload a single file or folder from internet। On the other hand, if one wants to upload multiple files at the same time, he should use SFTP to upload with a great ease. Through SFTP, interaction can be done.
It is very useful if one wants to control his computer remotely using the commands. With this we can manage our home computer from some other place. SSH provides a SECURED way to accomplish this.
We can setup SSH server in Windows using SSHd software.
1 ) - Download the setup of SSHd software and then install it.
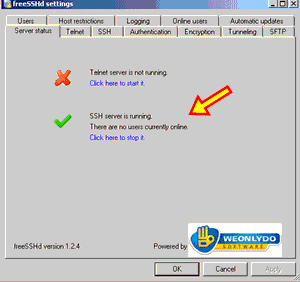
2)- Run SSHd. Double click the SSHd icon. SSHd icon will appear on System Tray. Then right click on the icon and then click settings.
3)- Create a new SSH user.
Click on the Users tab. You need to create one user account that will act as your SSH account.
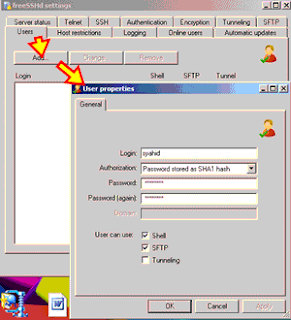
Cick “ADD” to create a new user. Enter the details of the user. Fill the username and the password. Click OK.
HOW TO ACCESS THE SSH SERVER-
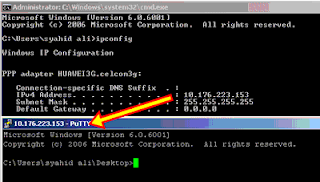
4)- Download PUTTY.
In the same machine, download Putty and install it.
It is a desktop command line client to access SSH server.
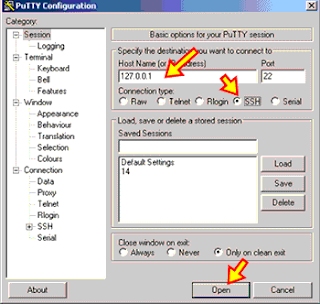
127.0.0.1 means that you are testing the SSH access from a local connection.
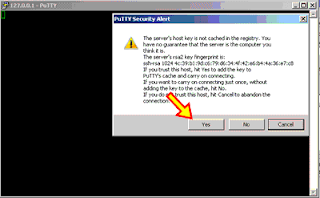
Press “Yes” on the security alert screen. Insert your SSH username and password that you have created previously.
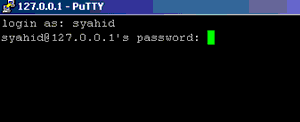
You should get a display line prompt. This means that you have successfully accessed SSH server.
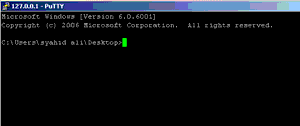
Connect computer to the some network and check your IP address.
5)- Test SSH
Use some other machine. Install Putty in it. Repeat the steps and use your SSh server IP address inside the Host Name.
You should again get a window display command prompt.
Setup SSH in LINUX.
We have to use sudo apt command for this purpose.
Type the following command to setup ssh server -
# sudo apt-get install openssh-server openssh-client
How to install ssh and run key command on it?
The server which we are using is called open ssh. We can use any version greater than 3.9 to install & run the command or upgrade our version.
To open ssh?
To make use of ssh first of all make an account on local machine as suso.org account.
To make real use of ssh server, supply the hostname as an argument.
Host name should be of the local machine on which you want to make account.
Such as:
ssh username@username.suso.org
Then press the YES button.
The authenticity of host can’t be established. RSA key finger print is- 53:b4:ad:c8:51:17:99:4b:c9:08:ac:c1:b6:05:71:9b.
Then a Message will appear-
Are you sure you want to continue connecting (yes/no)?
YES
Warning: Permanently added 'arvo.suso.org' (RSA) to the list of known hosts.
SSH's major features: Host validation. To put it simply, ssh will check to make sure that you are connecting to the host that you think you are connecting to. If someone wants to trick you into logging into their machine and neglect your ssh server, you will have some warning like this on to the terminal:
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@ @ WARNING: POSSIBLE DNS SPOOFING DETECTED! @ @@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@ The RSA host key for arvo.suso.org has changed, and the key for the according IP address 216.9.137.122 is unchanged. This could either mean that DNS SPOOFING is happening or the IP address for the host and its host key have changed at the same time. Offending key for IP in /home/suso/.ssh/known_hosts:10 @@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@ @ WARNING: REMOTE HOST IDENTIFICATION HAS CHANGED! @ @@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@ IT IS POSSIBLE THAT SOMEONE IS DOING SOMETHING NASTY! Someone could be eavesdropping on you right now (man-in-the-middle attack)! It is also possible that the RSA host key has just been changed. The fingerprint for the RSA key sent by the remote host is 96:92:62:15:90:ec:40:12:47:08:00:b8:f8:4b:df:5b. Please contact your system administrator. Add correct host key in /home/suso/.ssh/known_hosts to get rid of this message. Offending key in /home/suso/.ssh/known_hosts:53 RSA host key for arvo.suso.org has changed and you have requested strict checking. Host key verification failed.
If warning like this comes onto your terminal, then there is a reason for the local machine host key to change. If there is no good reason, then try to change the administration of local machine according to your requirement before connecting the machine. If you are trying to connect to your own computer, do some computer checking to determine the problem or check the I.P. address of your computer.
Then it will ask you for your password on the local system. If the username that you give is right and you type in the local machine password for it correctly then the system should let you in.
How to generate a key
On your local machine where you want your create key type the command
ssh-keygen -t dsa
If this is your primary identity key, make sure to use a good passphrase. If this works right you will get two files in your .ssh directory.
to use key:
scp ~/.ssh/id_dsa.pub burly:.ssh/authorized_keys2.
Now it is ready to accept your ssh key.
ssh-agent sh -c 'ssh-add < /dev/null && bash'
ssh-keygen -t dsa
It should begin spitting out the following:
Generating public/private dsa key pair. Enter file in which to save the key (/home/localuser/.ssh/id_dsa): Enter passphrase (leave empty for no passphrase): Enter same passphrase again: Your identification has been saved in /home/localuser/.ssh/id_dsa. Your public key has been saved in /home/localuser/.ssh/id_dsa.pub. The key fingerprint is: 93:58:20:56:72:d7:bd:14:86:9f:42:aa:82:3d:f8:e5 localuser@mybox.home.com
It will prompt you for the location of the keyfile. Ideally, you should choose something unique and un-guessable, just like your password, but it should be something longer, like a whole sentence. Here are some examples of passphrases :
The right thing changes from state to state
the purpose of life is to give it purpose
Some passphrases have as many as 60 characters along with punctuation and numbers. This makes the passphrase harder to guess.
HOW TO ACCESS A SSH SERVER:
There are two ways to access server-
1)- Command Line
2)- Graphical User Interface (GUI)
GUI- Graphical User Interface
It it is the interface which allows us to interact with the network using Graphical way, i.e, Images etc.
Text is not used in this type of interface.
It has advantage that one does not require to remember the complex commands.
We have some good GUIs.
For e.g. :
FileZilla is a good GUI. It can be run on Windows, Linux and even Mac. It is available in many languages. It has remote file access. Moreover it supports transfer of large sized files, may be greater than 4 GB.
We first have to create a certificate. This will be useful in Certificate Generator in FileZilla server.
Fill your details in the generator. Key size of the certificate is to be chosen. It may be 1024, 2048, 4096 bits. Larger the size, more is the connection secured. FileZilla need the paths to access certificate files. If we do not put the path, then later an error may come - "Could not load certificate file".
Put the file path to the private key and certificate files. After you have created the certificate enter its name and folder path location into the "Private key file" field or browse to it.
WIMP
GUI has a combination of elements.
A common combination of such elements in GUIs is the WIMP (window, icon, menu and pointing device).
WIMP uses an input device to control the cursor.
The information is represented with ICONS. The commands are compiled together and corresponding actions are performed.
GNOME-
It is also a GUI. It is capable of creating usable and high quality programs.
Command Line
In this type of interface, we have to type commands to interact with the network. First the user has to enter a command. Then a command line interpreter receives the command.
It executes the entered command. A terminal or a client is required to run a command-line interpreter. The output is return to the user in form of text lines.
To connect in Linux and Mac-
ssh -p 2222 cpanelusr@
Here, “cpanelusr” is the Username of the machine which we want to access.
Some other commands are-
# arch show architecture of machine
# cat /proc/cpuinfo show information of the CPU
# date show system date
# Made By: Akash Jain & Ankur Poria

No comments:
Post a Comment